EDI Protocol: What are the available options?
Today, EDI software is gaining wide recognition across the world. Be it a small-scale firm or large-scale industry, every business wishes to integrate their processes with EDI. But, before adopting EDI, they must have a brief knowledge of EDI protocol – a technology used by EDI to exchange the data.
In simple words, the EDI protocols are well-built software that determines how the business data will be transferred between the trading partners. Since their formation in the year 1968, they have seen many amendments. Several new elements were added to these protocols for every few years, to make them compliant with the newer technologies.
Topic Covered:
- What are EDI protocols
- What are the different types of EDI protocols?
- Direct Vs VAN
- HTTP EDI protocol
- AS1 protocol in EDI
- AS2 protocol in EDI
- AS3 protocol in EDI
- AS4 protocol in EDI
- x12 protocol
- FTP EDI protocol
- SFTP EDI protocol
- OFTP and OFTP2 EDI protocol standards
- REST API
- Web EDI protocol
- Mobile EDI protocol
Now, let’s try to understand what are EDI protocols along with their types and different applications in a quick manner.
What are EDI protocols
The EDI protocols are used to establish communication between different computer systems. To transfer business documents via EDI, both systems must utilize the same protocol. Each protocol specifies a set of standard guidelines that instruct how the data is encrypted as well as configured during the transferring process.
Several different types of EDI protocols are available and every EDI protocol offers multiple functionalities. Besides, each of these protocols facilitates successful communication within the organization as well as with n-number of trading partners.
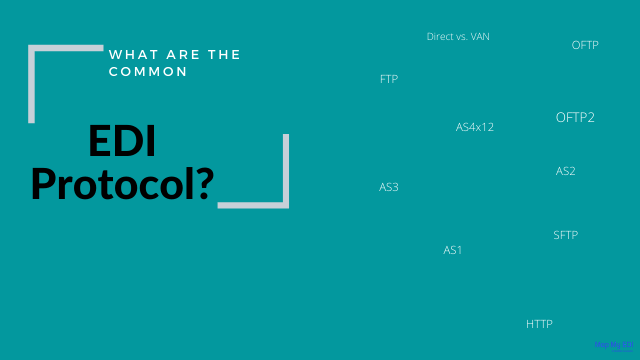
What are the different types of EDI protocols?
In the below list, we listed some of the most common EDI communication protocols. They are
- Direct vs. VAN
- HTTP
- AS1
- AS2
- AS3
- AS4
- x12
- FTP
- SFTP
- OFTP and OFTP2
- REST API
- Web EDI
- Mobile EDI
Now, let’s discuss the features and applications of each of these EDI protocols one-by-one:
Direct Vs VAN
In direct or point-to-point EDI, the connection will be established with a specific business partner by using a mutually-agreed protocol. On the other hand, with respect to VAN, there is no such kind of restriction. The VAN serves as a middleman between two systems and facilitates the successful transfer of business data. As a result, in this case, it really does not matter whether the EDI protocols used by both systems are similar or not.
Even though VANs were preferred earlier, the direct EDI started gaining more fame with the internet EDI. Usually, the initial setup cost is negligible in the case of VANs. But, it demands a considerable amount in the form of fees for every transaction.
On the contrary, if the business prefers direct EDI over the VAN, then it requires a heavy budget. Because the costs associated with setting up the EDI software and its regular maintenance are really high.
HTTP EDI protocol
Developed around 1991, Hypertext Transfer Protocol is one of the most popular EDI messaging protocols. It requires a web browser to transfer the data from one system to another. Any HTTP resource can be effortlessly located on the internet with the help of the Uniform Resource Identifiers (URLs).
Even though the HTTP EDI protocol is extremely simple to use, yet it lacks to secure the business data during the transferring process. Due to this, the usage of TLS or HTTPs is always recommended to enhance the performance of the HTTP protocol.
Further, HTTP does not have the ability to receive electronic receipts or to trace the data during the transferring process.
AS1 protocol in EDI
The AS1 stands for Applicability Statement 1 that instructs how to exchange the business documents safely and reliably. It focuses on the usage of email protocols (SMTP and/or S/MIME) for this purpose.
Developed during the 1990s by the working group of IETF, AS1 establishes web-based EDI communication among the systems. The features such as encryption, signing, or MDN conventions are utilized for this. Similar to the AS2 communication protocol, AS1 also demands the prior exchange of SSL certificates and names of specific business partners for transferring business data.
AS2 protocol in EDI
Similar to the AS1, the AS2 or Applicability Statement 2 makes use of the same features like encryption, signing, as well as MDN conventions. In this AS2 communication, the documents will be transferred via HTTP and/or HTTPS protocols. The digital signatures, receipts, or acknowledgements are used while executing this protocol.
Today, the AS2 EDI has gained quick popularity as it is used for point-to-point communication by many industries. It offers many advantages such as enhanced verification, high-level security, and real-time transactions.
Apart from these, the AS2 communication protocol also offers many benefits such as unlimited data exchange, 24-hour uninterrupted connection, and zero transaction fees. More importantly, the documents can be easily exchanged with any kind of file format.
In reality, no ERP software offers an inbuilt AS2 capability. But, the businesses can adopt this technology separately and gain the advantages of EDI via AS2. For this, they must own in-depth knowledge of the AS2 protocol’s functionalities.
AS3 protocol in EDI
Likewise, AS1, AS3 (Applicability Statement 3) is also developed by the IETF and is used by many industries that work with EDI FTP. It is an open-standard EDI transfer protocol that promotes secure data transfer and application interoperability.
The AS3 EDI file transfer protocol provides high-level security through implementing MDNs along with encryption. It is the most ideal option for businesses with sizable investments in IT.
AS4 protocol in EDI
The AS4 (Applicability Statement 4) is a web-services update of AS2 and can be easily implemented by the business with the least IT infrastructure. Since AS4 is an open standard EDI file transfer protocol, it is more compatible with standard environments as compared to AS2.
For any business, this AS4 protocol ensures highly-secured business data transfer. It makes use of encryption, password authentication, and digital signatures for this purpose. Besides, it also prevents data tampering during the transferring process and also confirms the authenticity of the sender.
Further, AS4 provides great support for the metadata and can easily transport any kind of payload. It also re-sends data in case of non-delivery, detects duplicates, and compresses large files. Besides, AS4 is regarded as the best option for both internal and external communications. The prime reason is, this EDI protocol maintains data integrity as well as confidentiality during the transferring process.
The AS4 is one of the newest and most-advanced EDI messaging protocols. A significant increase in its adoption can be seen these days as several businesses are looking to modernize their data communication systems.
x12 protocol
The x12 EDI protocol is specifically designed for the electronic transfer of machine-readable data between two systems. All the important data linked with order placement, processing, shipping, invoicing, and payment processing can be transferred with this protocol.
Developed by the American National Standards Institute (ANSI), x12 protocol facilitates interindustry electronic data interchange. Further, an affiliated institute of ANSI promotes, maintains, and also revises the related norms on a regular basis.
FTP EDI protocol
The FTP or File Transfer Protocol is one of the most used EDI protocol standards. It connects systems via the internet and facilitates secured data transfer by using separate control/data connections.
More often, FTP is used to transfer the data files within the programs for internal functions. Either user-password authentication or the anonymous user access will be enabled for this purpose. Further, this EDI protocol facilitates quick downloading of programs and other data files from a different server.
A typical FTP facilitates quick website updating and bulk file transferring. Also, it can be installed and used in multiple operating systems such as Windows, UNIX, Linux, as well as Mac OS. However, most businesses make use of FTP only for internal communication. For external communication, only the highly-secured EDI FTP is the best option even in comparison with the AS2 FTP.
Even though FTP is not a secure communication protocol, it provides verification functionality when it gets the support of AS2. With it (widely known as AS2 FTP), businesses can exchange both EDI and XML documents.
SFTP EDI protocol
The Secured File Transfer Protocol (SFTP) is an extension of SSH version 2.0. It facilities quick file accessing, file transferring, as well as file management functionalities.
These days, the SFTP protocol is mainly used in two ways. One, it is used as over Transport Layer Security (TLS) and two, to transfer management data within VPN applications.
OFTP and OFTP2 EDI protocol standards
The OFTP or Odette File Transfer Protocol has been specifically built to facilitate the B2B business data. It is one of the simplest protocols since it makes use of only 14 commands and established point-to-point connections.
Regarded as the highly efficient EDI protocol, OFTP allows easy transferring of massive data. The OFTP2 is a newer version of this OFTP that facilitates the secured data transfer over the internet (X.25 and ISDN networks).
Both EDI protocol standards provide electronic delivery receipts. Also, they can easily work with VAN and point-to-point EDI. But, OFTP2 offers more features over OFTP. For instance, data compression and digital certificate exchange. Also, it supports regional languages (Japanese and Chinese) and the easy handling of massive business data.
REST API
The Application Program Interface involves a set of rules & mechanisms that instruct how two systems will be connected for data sharing. Once the setup has been installed, the data can be easily accessed whenever it is required even in the absence of the main business/trading partner. Also, with this EDI, the role-based access control can be imposed.
The REST API is one of the best EDI protocols as it facilitates the flexible transferring of business data. However, an API management layer is needed if the trading partners’ network is large. It also requires expertise in web programming in case the EDI is handled in-house.
Web EDI protocol
The web EDI is one of the modernized EDI communication protocols. With the help of an Internet Browser, significant business data can be transferred by creating online forms. These forms will replicate the paper-based documents and facilitate easier contact between two systems.
Each form contains numerous fields where the users can enter the specific data. These forms will be converted into EDI documents automatically through secure internet protocols. For example, AS2, FTPS, or Hypertext Transport Protocol Secure (HTTPS).
Usually, the web EDI file transfer protocol functions around the famous hub-and-spoke model. Here, the main business serves as the hub and its trading partners act as spokes. The hub implements the EDI by developing web forms that are hosted on the hub’s website. Then, trading partners enter business data into these forms that are processed by the hub after converted into EDI documents.
Any small or medium-size business can leverage the benefits of this EDI protocol. It is an ideal EDI transfer protocol for such businesses since there is no need for any installation and maintenance. Further, it can be extended to a trading partner located in another part of the world and has limited IT capabilities.
Mobile EDI protocol
The EDI system wireless application protocol is the latest addition to EDI protocol standards. As more businesses are looking to ease their supply chain processes, new mobile EDI apps are being developed. Most of these apps are compliant with smartphones and tablet phones.
The best example of this kind of EDI protocol is the Direct Exchange (DEX). It is mainly used in the retail industry where the delivery person scans the item’s barcode into the mobile device to generate the invoice. The data quickly gets transferred to a receiver through in-store docking stations. This receiver opens the invoice available in the docking system and verifies the order details.
Once the data match, a finalized copy will be sent to the supplier system through the mobile system. A considerable amount of time and effort can be saved with this technology adoption.
For any business, it is better to conduct detailed research before integrating EDI with its processes. It must check its technical infrastructure and budget constraints. Even it can set up hybrid communication if required.
A powerful EDI protocol establishes seamless business communication. So, businesses must choose an EDI solution wisely by taking all the key aspects into consideration.
Read Related Articles: